
Introduction
Hello friend,
today let's examine computer networks. To connect a service to a remote host, we first have to determine whether this host is alive and reachable. To do so, the
icmp protocol was introduced and defined in 1981.
There are various status information that can be written in an icmp packet,
see wikipedia for a list of them. The probably most known and widely used service is
ping, or type 8. To ping a device, we send a type 8 packet to it, and it either responds with 0 (alive), is unreachable (no answere) or discards our packet (same as unreachable).
Why keep track about icmp packets?
As said, ping is used to check which devices are alive in a computer network. This means that an attacker would probably use ping in some form (well, actually there are other means of detection, but let's keep it simple for now). So knowing who is pinging our computer would give us a basic understanding about who is gathering information about us. Some dudes have programs that ping over the whole ip range all the time, creating more or less "live maps" of the internet.
Another thing is that the icmp protocol can be abused for ddos attacks against a specific device (or server most of the time). Logging these attacks can probably not detect who was causing them, but it might give us a better understanding about the attack. For example, if most of the ips pinging our network came from brazil, this might give us a clue where the attacker is located and which packets we might consider blocking at backbone level.
Setup a simple ping-tracker
While there are other, more efficent ways to keep track about pings, namely log-files and programs like wireshark, let's setup a simple linux one-liner to monitor pings at real-time. This is far away from a real security solution, but it should do the trick for monitoring bad neighbours and the like.
We are using the built-in sniffer tcpdump that should be available in most UNIX and linux systems.
The command is
tcpdump ip proto //icmp
As you might guess, there are other packages and protocols available that we can sniff.
Ubuntuusers has a nice list about which parameters are available for tcpdump.
For example, the network stack could be monitored by using the -S flag to monitor the absolute sequence number of the packages. Play around with the program and try to find the best solution for whatever you want to achieve, we are for now only monitoring pings against our system.
Test our setup
So, as all is setup and ready to go, let's try out our sniffer.
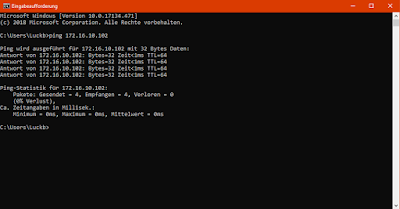
To demonstrate it, I used a normal windows mashine and pinged my linux computer:
The host is answering normally and we can not know whether it noticed our ping, so everything works as expected here.
And what's going on at the linux side? Let's see:
Yes! We noticed that someone pinged us and can now decide whether we want to investigate or ignore it. As the ip is in our local network, we can assume the mashine pinging us is not that far away from our physical location, so let's have a talk to our neighbours and find out whether they where just curious, or maybe someone broke into their mashines and pinged us without their knowledge.
That's it, cybermonkeys. You can now keep track about incoming pings and get paranoid if you want.
Never tell anybody your password.
Except they offer you candy.
- numb.3rs


Comments
Post a Comment